
Over the last few days we have seen a wild ride with respects to sites being compromised. We have seen Core Security compromised…or not.
“There is nothing of importance posted here. Core’s active servers, websites or networks were not compromised nor did the information recently posted contain information residing on those systems. In fact, the information is from a third-party server with content of no value, that has not been used for at least 8 years. To be clear, there was no confidential information accessed.”
The UFC, Dreamhost (pain in my ass), Onguardonline.gov and the venerable Zone-H to name a few, were also spanked by hackers.
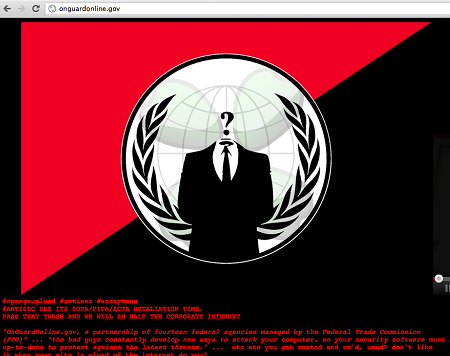
Last night, as I “enjoyed” my insomnia, I was tipped that the FTC site Unguardedonline.gov onguardonline.gov was compromised by the group Anonymous, or rather a subset of that group called Antisec.
From CSO:
Hackers under the AntiSec banner appeared to have hacked late Monday the website of OnGuardOnline.gov, the U.S. federal government’s online security website, in protest against controversial legislation.
In a message on the OnGuardOnline website and on Pastebin, the hackers threatened “a relentless war against the corporate internet”, destroying what it said would be “dozens upon dozens” of government and company websites, if the Stop Online Privacy Act (SOPA), Protect IP Act (PIPA) and Anti-Counterfeiting Trade Agreement (ACTA) are passed.
Again…how is this supposed to help their cause?
The defacement mirror Zone-H was the next heads up that I received a few minutes later. Nothing like biting the hand that feeds. I seem to recall that type of behaviour helped to bring about the end of the mirror site Alldas.de back in ’01.
Then, the death of my Saturday, DreamHost got pwned.
IMPORTANT INFORMATION: We are writing to let you know that there may have been illegal and unauthorized access to some of your passwords at DreamHost today. Our security systems detected the potential breach this morning and we immediately took the defensive precaution of expiring and resetting all FTP/shell access passwords for all DreamHost customers and their users. There are three different types of passwords at DreamHost: a web panel password (for logging into the panel), email passwords, and FTP/shell access passwords. Only the FTP/shell access passwords appear to have been compromised by the illegal access. Web panel passwords, email passwords and billing information for DreamHost customers were not affected or accessed.
Yet, on their website they said the attack was blocked at first. “Our intrusion detection systems alerted our Security team to the potential hack, and we rapidly identified the means of illegal access and blocked it.“. If that were true I would not have had to spend my Saturday changing passwords. In the same posting they also “suggested” changing passwords for email accounts. “However we recommended in an update email to customers and their email users late yesterday that they reset their email passwords as well, as a precaution.”
And the passwords that were purloined…were unencrypted.
Fantastic.









