
A quick heads up for our readers. LinkedIn appears to have had their passwords dumped and people are popping them with reckless abandon.
Rough 24 hours for LinkedIn. Just yesterday we heard that opt-in folks were having their calendars uploaded in…plain text. Maybe they can search their job postings for some security folks.
Too soon?
CHANGE YOUR PASSWORDS!
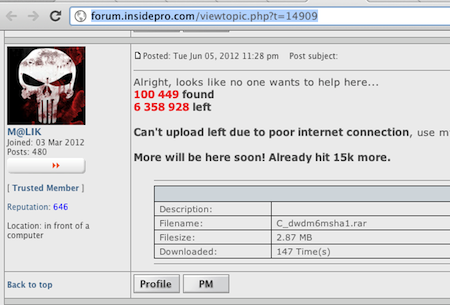
We have a copy of the dump file and are examining it.
Interesting to note that LinkedIn released a new version of their iOS app with a fix for the plain text calendar issue and “bug fixes”. Wonder what that entails?
UPDATE: Wednesday 3:32 pm. From LinkedIn:
Our security team continues to investigate this morning’s reports of stolen passwords. At this time, we’re still unable to confirm that any security breach has occurred. You can stay informed of our progress by following us on Twitter @LinkedIn and @LinkedInNews.
When asked for comment, the rest of the Internet said, “Um, yes, it really has”.
Also, from Errata Security, they have a tool to test LinkedIn passwords. Be sure to reset yours BEFORE using anything like this. And never…never use that password again.
It is also interesting to note that the share price of LinkedIn appears unaffected for the most part. The share price was only down $0.44 at the time of this writing (3:38 pm EST). Markets do not understand data breaches the way they should.
UPDATE 2: At 3:41 pm we noticed that LinkedIn has finally come clean about the breach. It would have been really difficult for them to stick their fingers in their ears and say “Nah nah, we can’t hear you” for much longer.
From LinkedIn:
We want to provide you with an update on this morning’s reports of stolen passwords. We can confirm that some of the passwords that were compromised correspond to LinkedIn accounts. We are continuing to investigate this situation and here is what we are pursuing as far as next steps for the compromised accounts:
Interesting side note…only affected users to be emailed?
These members will also receive an email from LinkedIn with instructions on how to reset their passwords. There will not be any links in these emails.
If anyone gets one of these emails please drop us a copy at “tips AT liquidmatrix DOT org”.
Read on for the full posting. (h/t to @securityninja)
Check out LeakedIn.org for compromised passwords.
Source: Article Link
(Image used under CC from Darwin Bell)









