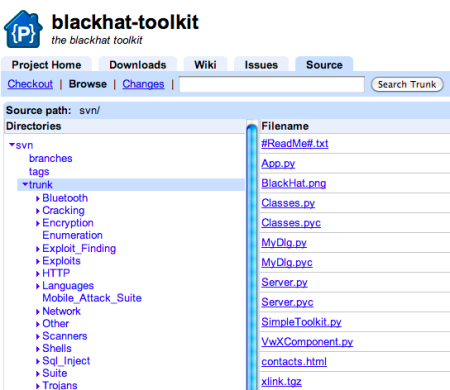
So, Google it seems being leveraged to host malicious code. No shock there. The code in question in this case is a toolkit referred to as the “Ultimate BlackHat Tool Kit” which web delivered collection of applications and scripts that are a few years dated.
From Websense:
Last week, the media picked up that the Google Code project Web site is used to host malicious files. I decided to have a look at what kinds of malicious Web-based code Threatseeker has detected on the site. In particular, one interesting example came up: one of the pages hosted on Google Code was a PHP-based Web console code
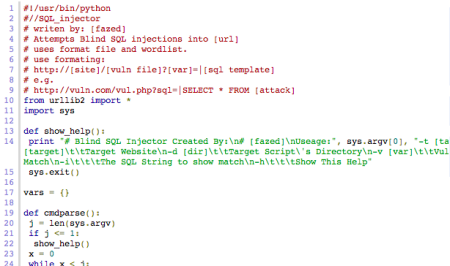
Here is a sample of one file.
At the writing of this post the site was still live. You can check out a copy with svn. The repository has been online since 2007 by the looks of things. Originally posted by a group called team.netaware. The primary author appears to be a character by the name of [fazed].
Have a look. No idea how long it will be before Google gets around to shutting it down. After all its been online since 2007.
And as a parting shot I can’t help but to giggle at this passage…
To help protect users against malware threats, Google has built automated scanners that detect malware on websites we’ve indexed. Pages that are identified as dangerous by these scanners are accompanied by warnings in Google search results, and browsers such as Google Chrome, Firefox, and Safari also use our data to show similar warnings to people attempting to visit suspicious sites.
Which was originally posted on Google’s security site in Oct 2009.









